Recently, one of my relative has been victimized by an unknown person by the means of some cyber crime techniques . Now a days , The Number of web users are increased so crime related to web technologies ,also increase. Because of unawareness of cyber crimes , innocent people are victimized . Here, i am trying to aware about some crimes sothat you can save your data, personal information, money etc.
The techniques are:
1. Social engineering
2. Phishing page
3. Key logger
4. viruses, web worms , malwares .
5. cookies
1. Social Engineering:-
People are tricked into performing actions they would not otherwise want to perform. that is, By some social medium , somebody try to force you do to some wrong action so that hacker can get access to your computer, account or anything. there are a lot of methods for this some are
fake codec:– During your browsing , suddenly some message come(prompt) and message may be say that you need to download that file for some purpose but actually that file may be a virus, trojan or any other malicious code which let hacker to connect your computer with hacker’s computer. So do not download any unknown file which you do not know.
malicious peer to peer files: – there are some sides which support peer to peer file sharing system like utorrent, Bittorrent , pando etc. sides which let you download the files which are shared by someone else like you . so it is more chance to add viruses , trojans with there movies files, songs files , software files etc. and when we download that file that malicious code can be installed in your system.
malicious updates: some time , during browsing , some updates may be come like operating system updates , browser updates or ay scanner for scanning your pc for virus . these all can be a trap for you. actually this type of updates may be some malicious code which can infect your PC as well.
fake calls:– Somebody can call you as an employee of any bank, organization or any hospital etc. he may ask your personal details .
fake person:- some time , for a short time like journey in trains, buses, any seminar , you can make friends . after one or two hours somebody can ask you about your mobile number, facebook id etc. If someone knows about your personal details like your parents name , number of brother sisters , date of birth etc. then he can go to your side and click on password forgot button . Then Computer will ask about the personal question which you wrote at that time when you created your account. If that question you gave same which that hacker knows , he can access your account. so be sure when you meet any stranger , do not reveal all the information .
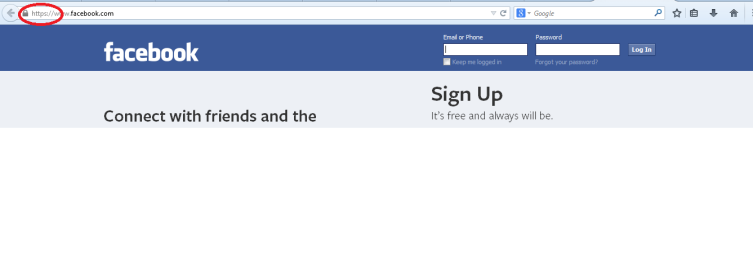
2. Phishing page :-
Phishing is the act of attempting to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication. that is, a webpage which is looking like a standard any perticular website but it is not actual web page ,it is made for getting whatever you will write in that webpage.
Example: suppose you are browsing facebook page . you find that page by searching on google. may be that facebook page is fake. when you write your user id and password it will go to the hacker’s computer.
3 key logger:- Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (or logging) the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware that their actions are being monitored.
Whenever you use other’s computer , be sure that this computer does not have key logger . otherwise whatever you will press on keyboard everything will save on a file and after that that person who installed that keylogger can read what you typed on that computer. there is also a keylogger plug-in by mozila firefox so just see all the plug-in in your browser whether any keylogger is installed or not.
4. virus, malware, web worms :
Do not open untrusted sites, malicious sites or other those sites which are banned and Do not download and install any file from untrusted sources.
5. cookies:Cookies are usually small text files, given ID tags that are stored on your computer’s browser directory or program data subfolders. Cookies are created when you use your browser to visit a website that uses cookies to keep track of your movements within the site, help you resume where you left off, remember your registered login, theme selection, preferences, and other customization functions. So always clear your cookies , if someone can access your cookies he or she can find a lot of information about you.
How you can save your self:
1. your awareness
2. digital certificates
3. https
4. anti-virus
5. turn-off java-script
1. Awareness :- If somebody ask you about your personal information , you should firstly think that how can you trust him . do not say any information to strangers . Do not say your password of bank account , facebook account or any type of account , if someone ask you about your password then you can be 100% confirm that he is a fraud.
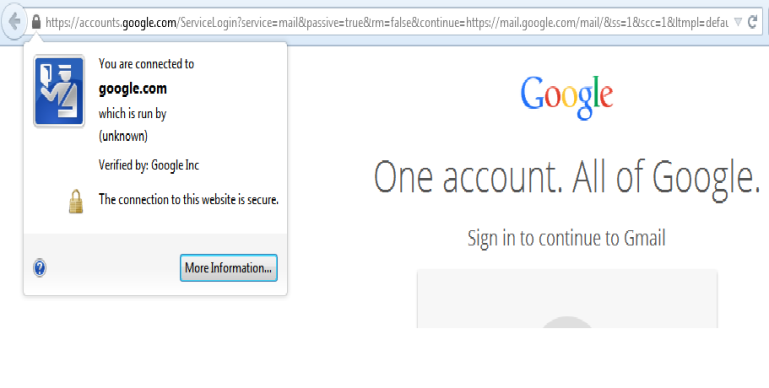
2. Digital certificates :-
Now a days, every good website has digital certificates . Digital certificates means there are certain organization which give certificates to only secure sites so that people can trust on these type of sites.
3. https:
https protocol using sites always be trusted so just remember that if you are going to transfer any money see the protocol name on the address bar.
4. anti-virus:
You should always have a good anti-virus and you should also update that anti- virus frequently . without updating of your antivirous can fight with only those viruses which were in the past . By updating your anti-virus , you make it strong and able to fight with latest viruses .
5. turn off javaScript :-
In normal browser always turn off your javaScript . because maximum viruses are written in javascript on web .
If you are victim of any cyber crime then you need to write F.R.I. in your local police station and you can also contact with cyber cell .
this is the link where you can find all details regarding cyber cell:
http://infosecawareness.in/cyber-crime-cells-in-india
BE AWARE BE SAVE………